Keep your S3 buckets safe from malware! GuardDuty scans new and updated files uploaded to your chosen Amazon Simple Storage Service (S3) bucket. This automatic scanning helps identify potential malware threats before they can cause harm.
In this blog post, I will walk you through a step-by-step guide on how to deploy AWS Guard Duty malware protection for S3.
Configuring Guard Duty Malware Protection
Navigate to the AWS portal, and search for guard duty.
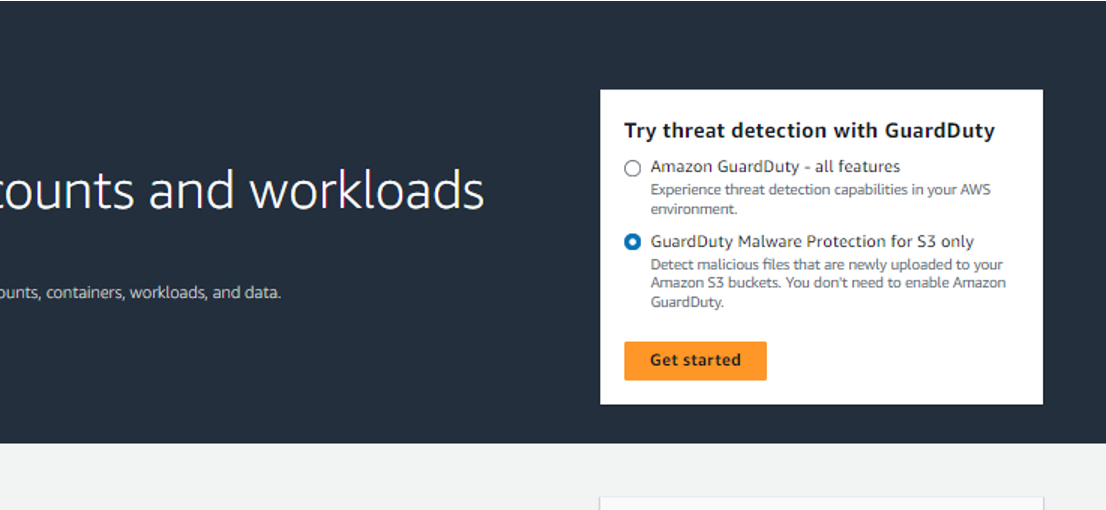
On the guard duty home page, click on “Get Started” after selecting the radio button next to the “Guard Duty malware protection for S3 only”.
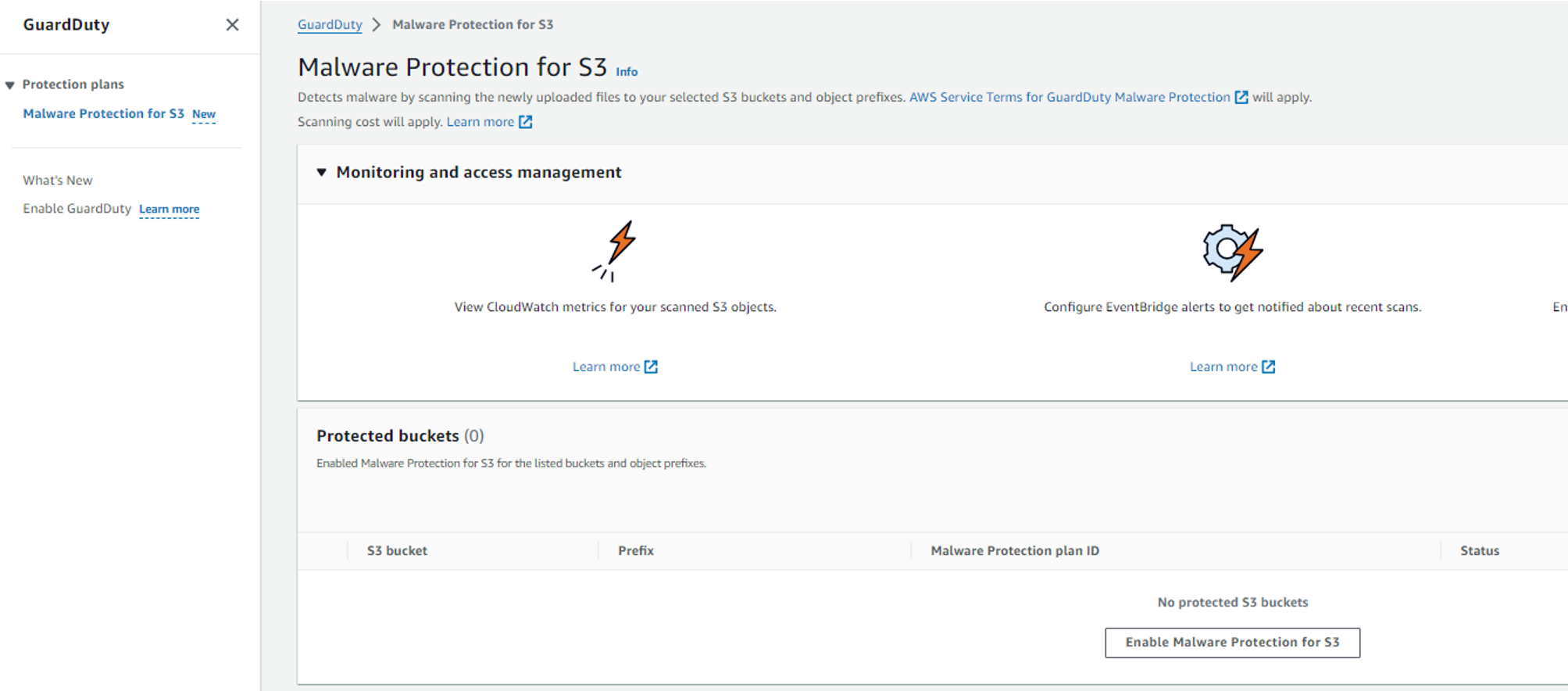
You will be redirected to the Guard duty console where we need to enable the S3 bucket configuration.
Under the “protected buckets” section click on “Enable malware protection for S3”.
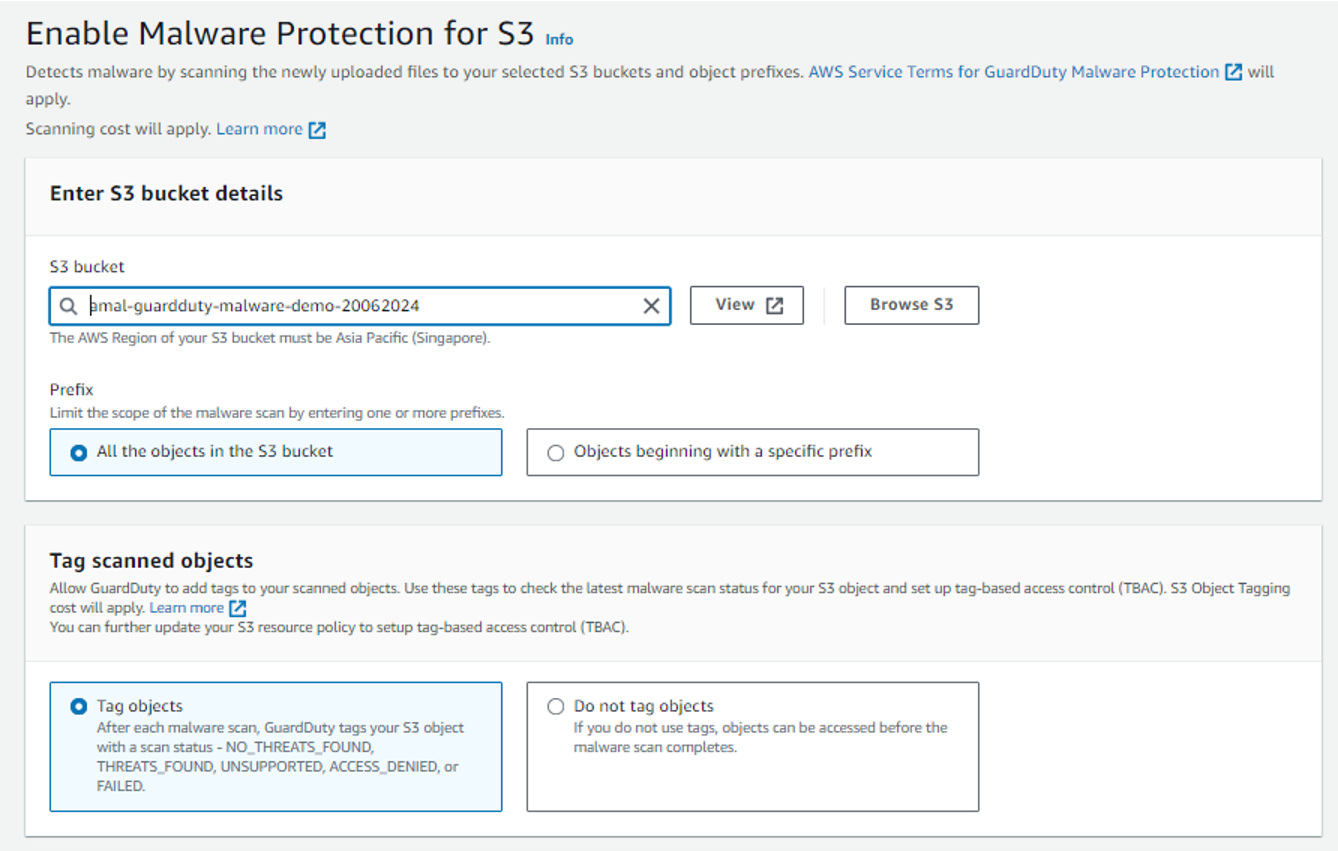
In the “Enable malware protection for S3” wizard, select the S3 bucket you need to protect using Guard Duty. You can click on “Browse S3” and select the bucket you need to protect.
You need to do this exercise repeatedly if you have multiple buckets to add.
Under the prefix, you can select the radio button if you want to scan all the files or any specific types of files.
Under “Tag scanned objects” select the radio button next to the “Tag objects”.
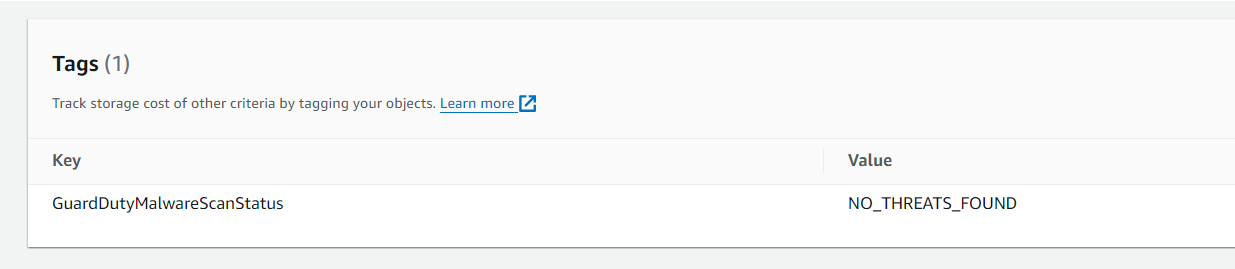
The objects will be tagged as “THREATS_FOUND” if guard duty detects any file containing malware. It will tag the devices without malware as “NO_THREATS_FOUND”.There are additional object tags like ACCESS_DENIED or FAILED based on the scan result.
Guard Duty needs IAM permissions such as Read/Tag S3 objects, send to event bridge, and more. The pre-configured permission JSON file can be copied from the “View permissions” option under “permissions”.
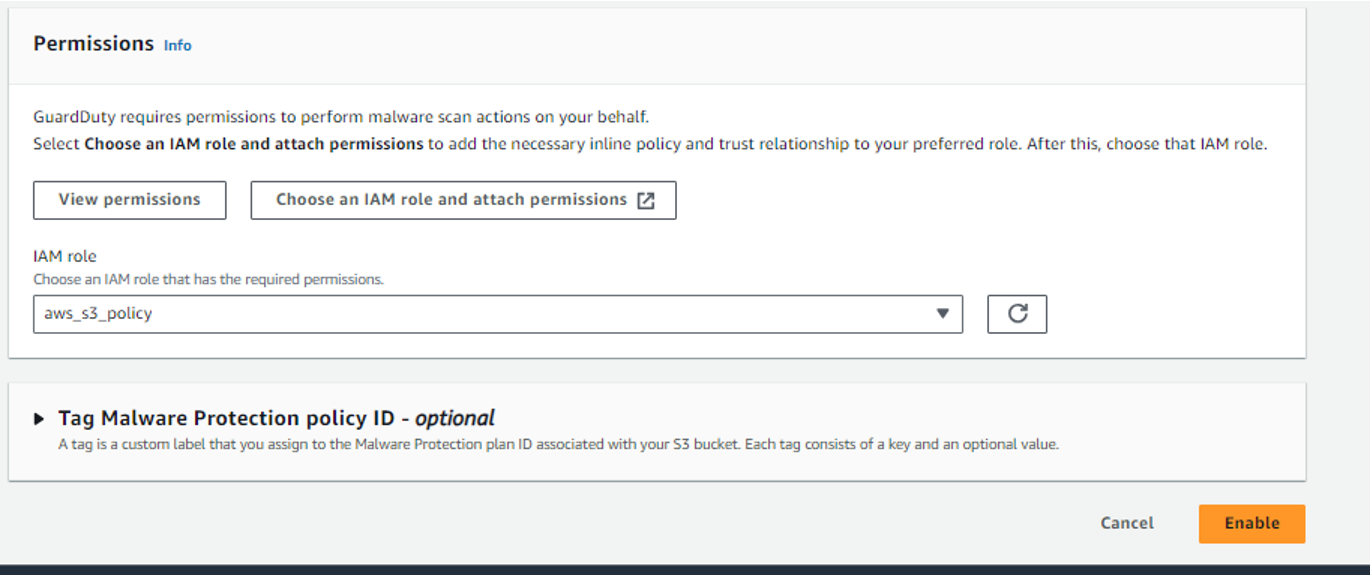
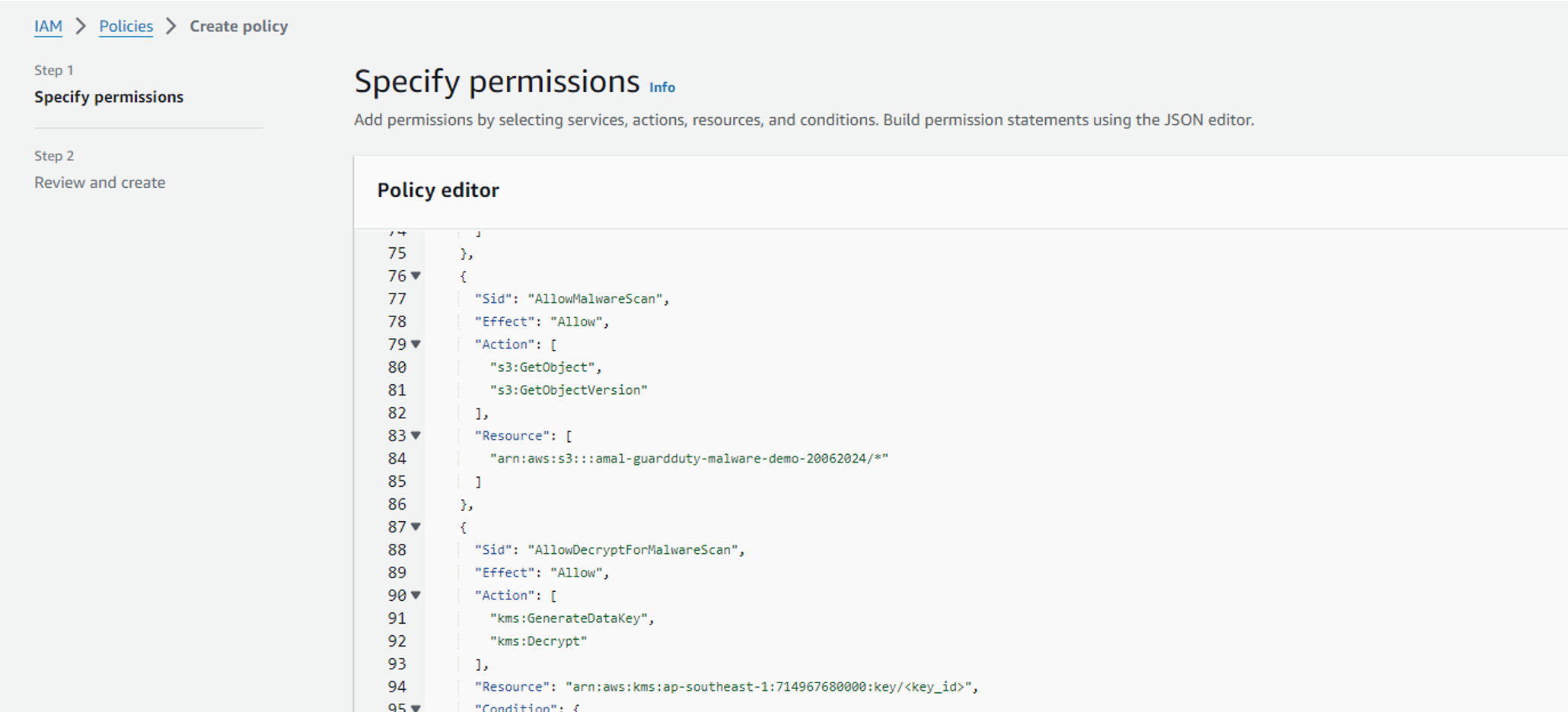
First, create an IAM policy and copy the contents from the JSON file. Once you create the policy, the policy needs to be linked to an IAM role.
The IAM Role trust entities need to be configured to allow the “malware-protection-plan.guardduty.amazonaws.com” Service as shown in the screenshot below.
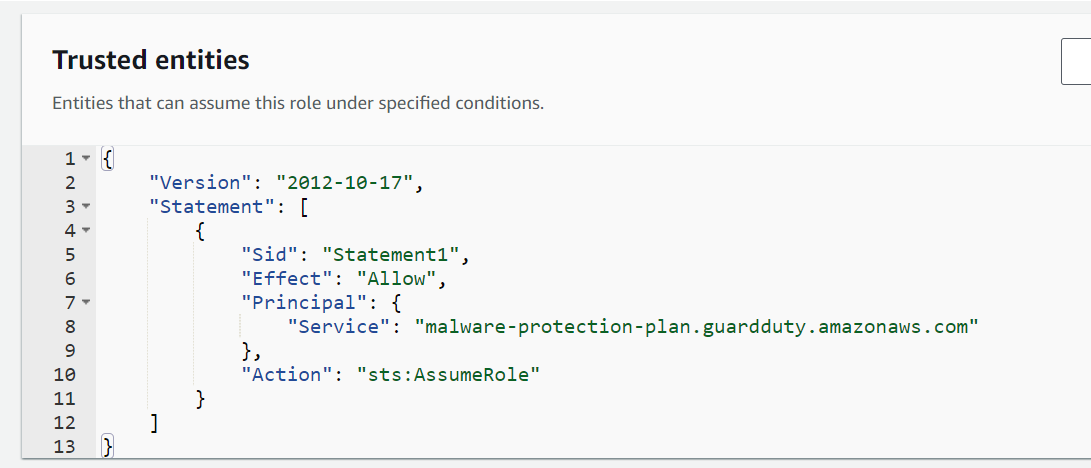
Click on “Enable” to enable the protection.

Testing the Functionality.
“Important Note: Uploading actual malware is not recommended as it could be harmful. To test GuardDuty functionality, we can leverage a safe test file provided by the European Institute for Computer Anti-Virus Research (EICAR) specifically designed for this purpose. Download the test file from the EICAR website.
I uploaded the test malware file to my S3 bucket. The guard duty scanned the file and created a tag with the key pair as {“GuardDutyMalwareScanStatus”: “THREATS_FOUND”}.
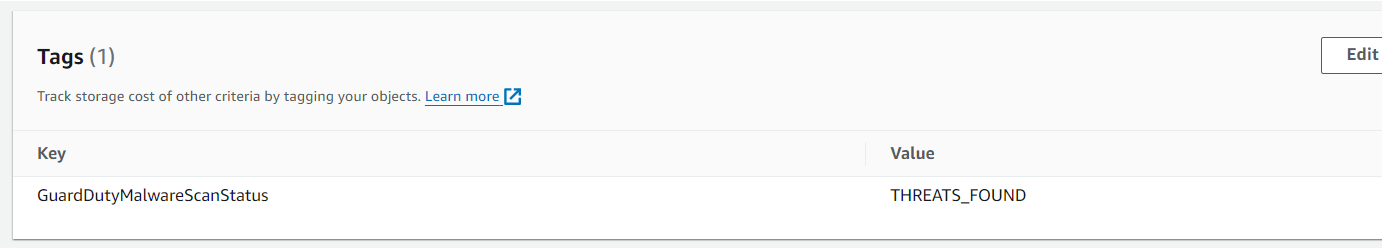
I tested by uploading a normal file without any malware and the guardduty created a tag with the key pair as {“GuardDutyMalwareScanStatus”: “NO_THREATS_FOUND”}.
We can configure Quarantine rules via event bridge and lambda to move the malware files to a different S3 bucket created for Quarantine or to delete them immediately.
Guard Duty malware Protection for S3 pricing
Guard duty malware protection for S3 charges you $0.60 per GB and also $0.215 per 1000 PUT requests.
Hope the blog is informative, please feel free to share your comments
